Resource library

Discover a new approach for provisioning that leverages machine learning and AI to automate this historically tedious process.

The Blue Ridge Bank infosec team sought to improve the accuracy of user access reviews, which had been performed manually to achieve the required ...

Experts discuss the results of the recently-conducted market research of identity leaders, and IGA best practices for 2025.
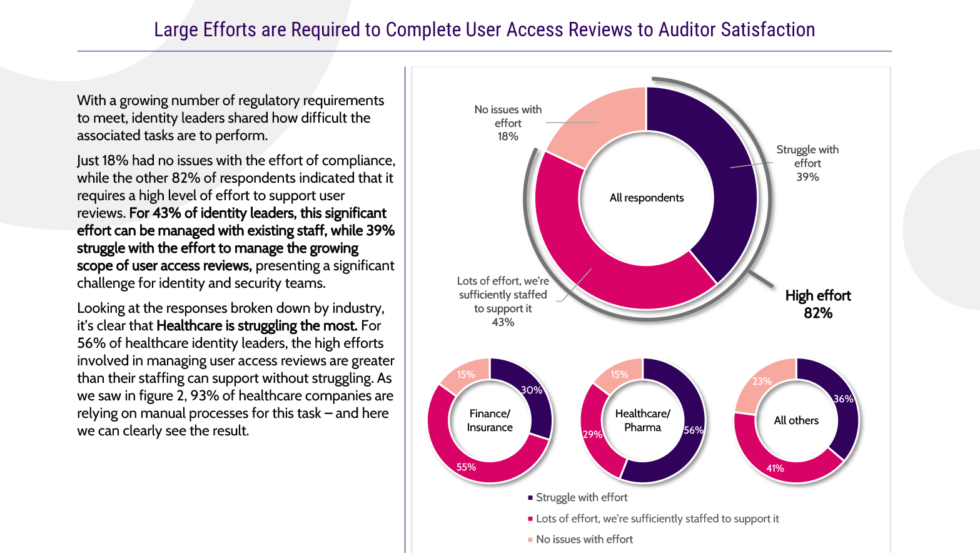
We embarked on a survey of 300 identity leaders to uncover the true state of identity governance in today’s enterprises. Get the findings.

After quickly deploying Zilla Security, Sprout Social saw a 75% reduction in project duration of access reviews, along with other improvements.

The Linux Foundation uses Zilla’s Modern IGA Platform to automate access reviews and gain entitlement visibility across their SaaS, and homegrown apps.

IGA pioneer Deepak Taneja and identity expert Paramita Chakraborty from GuidePoint Security explore the challenges with legacy IGA today.

Stop drowning in user access reviews and provisioning tickets. Meet Zilla’s breakthrough automation for identity governance.

A modern IGA solution is essential for security, compliance and operational efficiency, and the IGA automation avoids the challenges of legacy IGA deployments.

Zilla AI Profiles lets teams automate most of the manual work associated with managing roles, dramatically simplifying identity governance.

The traditional security perimeter is evolving as applications, remote access needs, users, and permissions continue to proliferate in the enterprise.

Marco Palella discusses how the software supply chain gets exploited by malicious actors and what companies can do about it.

Nitin Sonawane and Paul Roberts discuss the connection between digital transformation, identity, cloud, and software supply chain risk.

Dive into the essentials of user access reviews through the eyes of the auditor.

Navigate the dynamic landscape of governance, risk, and compliance (GRC), that are sure to shape the second half of 2024.

Deepak Taneja and Jonathan Keith discuss key challenges and strategies for effective identity management in the cloud.

Zilla Compliance is your path to audit-ready compliance for the cloud era.

Zilla Provisioning makes access provisioning easy, fast, and secure, and provides enterprise-ready self-service access provisioning.

Zilla Security is your defense against data breaches and ransomware incidents that have identity security roots.

Weichert, a national real estate provider, utilized Zilla Security to automate access review tasks, improving efficiency and security in managing user ...

Hippo Insurance Services used Zilla to reduce the heavy lift of compliance and governance by automating over 90% of the access review tasks.
A guide to the often-overlooked intricacies of human and non-human service account management.

The talk aims to shed light on the risks businesses may face if they fail to follow the best SoD practices. Explore the real-world implications of ...

Understand how Colonial Pipeline fell prey to a costly ransomware attack by neglecting to disable an inactive user account properly.

Join Dan Peterson, a product strategist at Zilla Security, for an introduction to the evolving best practices in identity security management.

Delve into the challenges and opportunities of identity management in the cloud era. Part one of a two-part conversation.

In this tech talk, Zilla Sales Engineer Marco Palella discusses six best practices you can apply immediately to protect your AWS infrastructure. They were ...

In this webinar, Deepak Taneja, the CEO and co-founder of Zilla Security, joins Paul Roberts, the editor-in-chief of The Security Ledger to discuss the ...

Delve into the challenges and opportunities of identity management in the cloud era. Part two of a two-part conversation.

This ROI study reveals the time and cost savings that a 400-employee company with 25 applications achieved by using Zilla’s access review platform. The ...
No results found.